Access Internet from Private Subnet in VPC
I’m finally forced to learn the network configuration stuff in AWS VPC. The thing that was confusing me was the NAT Gateway.
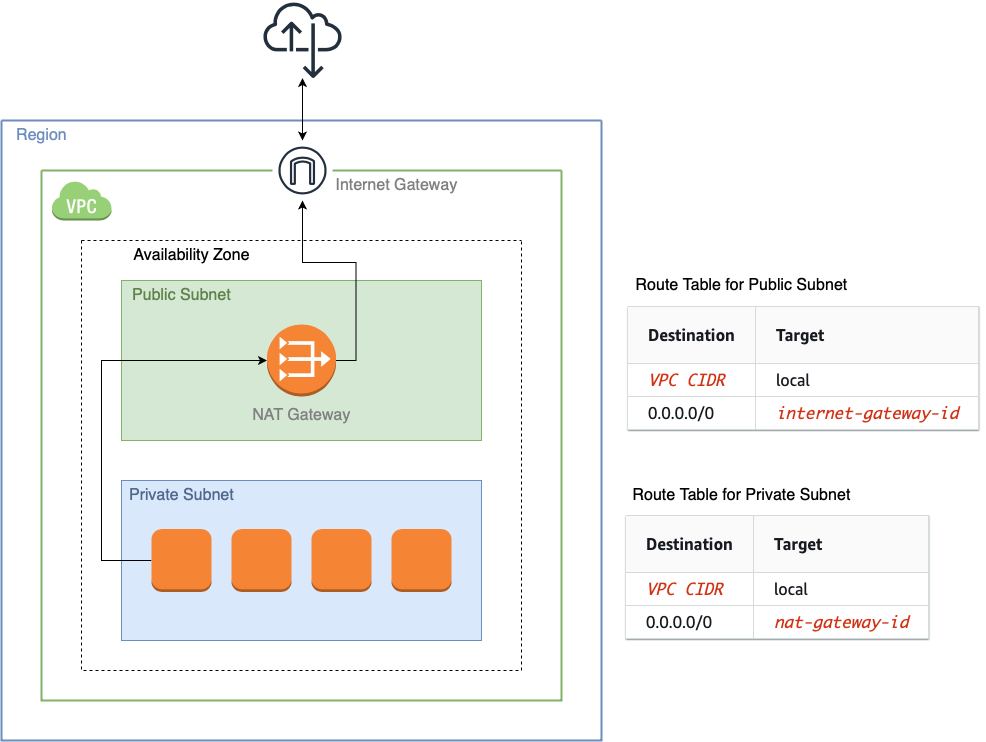
For a private subnet to access the internet, we route traffic from the private subnet through a NAT Gateway which keeps out all traffic initiated from the internet. This gateway needs to be in a public subnet, so that it can access the internet through the Internet Gateway.
To route the traffic in this way, we need to make sure there’s an entry in the route table for the public subnet to connect to the Internet Gateway, and there’s an entry in the route table for the private subnet to connect to the NAT Gateway.
Step 1: Create VPC, Public and Private Subnets
Create public and private subnets for each availability zone. Make sure that the subnets don’t overlap. For an explanation of subnets and CIDR notations:
Step 2: Create Internet Gateway and NAT Gateway
Make sure to create the NAT Gateway for each availability zone, and make sure they are created in the public subnets, select “public” connectivity type, and allocate an elastic IP Address.
Step 3: Create Route Tables
For each public subnet, create a route table, add an entry to connect to the internet gateway, and associate it to that subnet.
For each private subnet, create a route table, add an entry to connect to the NAT Gateway in the same availability zone, and associate it to that private subnet.
Step 4: Add access to AWS resources
If we want the subnets to have access to AWS services such as S3, we can create an endpoint for AWS services, and associate that endpoint to the route tables we created above.
Step 5: Make Sure Network ACL and Security Groups Don’t Block the Internet Traffic
When selecting security groups to use for services launched in the private subnet, make sure it allows traffic from and to the NAT Gateway.
I was tripped up by this when setting up network connections for EMR Serverless.